 Source: tse1.mm.bing.net
Source: tse1.mm.bing.netIn today's interconnected world, remote access to computers has become an essential need for many individuals and businesses. Whether you want to assist a friend with their computer issues or access your work computer while traveling, the ability to connect to another computer remotely can be incredibly convenient. In this article, we will explore various methods and tools that allow you to access another computer remotely over the internet.
What is Remote Access?
 Source: tse1.mm.bing.net
Source: tse1.mm.bing.netRemote access refers to the ability to control and access a computer from a different location using a network or the internet. It allows users to interact with another computer as if they were physically present in front of it. This capability has numerous applications, from providing technical support to accessing files and applications on a remote machine.
Understanding the Basics of Remote Access
 Source: tse1.mm.bing.net
Source: tse1.mm.bing.netTo access another computer remotely, you need two key components: a client and a host. The client is the computer from which you want to connect, while the host is the computer you want to access remotely. Both the client and host need to be connected to the internet for remote access to work.
There are two primary methods of remote access: unattended access and attended access. Unattended access allows you to connect to a remote computer without the need for anyone to be physically present at the host machine. On the other hand, attended access requires someone at the host computer to grant you access by accepting the connection request.
Methods for Remote Access
1. Remote Desktop Software
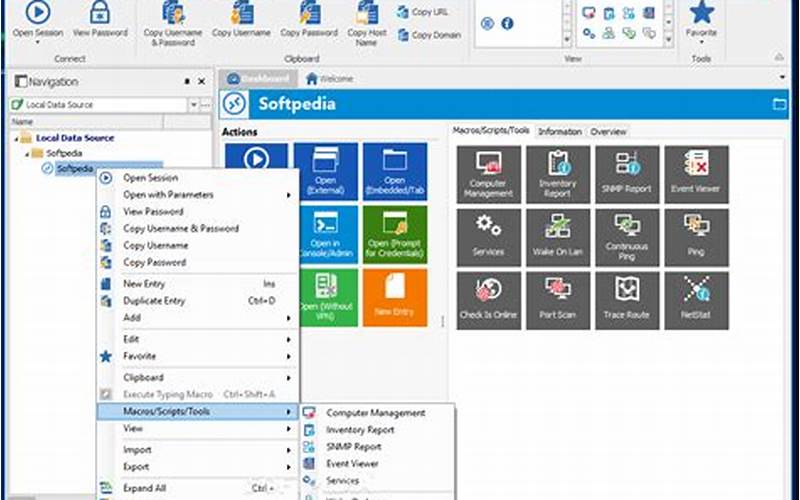 Source: tse1.mm.bing.net
Source: tse1.mm.bing.netOne of the most common and user-friendly methods for remote access is through remote desktop software. This software allows you to control a remote computer as if you were sitting in front of it. Some popular remote desktop software options include TeamViewer, AnyDesk, and Chrome Remote Desktop.
Remote desktop software typically requires both the client and host to have the same software installed. Once the connection is established, you can control the host computer, access files and folders, and even transfer data between the two machines.
2. Virtual Private Network (VPN)
 Source: tse1.mm.bing.net
Source: tse1.mm.bing.netA Virtual Private Network (VPN) is another method for remote access that provides a secure connection between your client and the host computer. A VPN creates a private network over a public network, encrypting your data and ensuring privacy and security.
To access another computer remotely using a VPN, you need to set up a VPN server on the host computer and configure the client to connect to it. Once connected, your client will be assigned an IP address on the same network as the host, allowing you to access resources as if you were physically present.
3. Remote Access Tools Built into Operating Systems
 Source: tse1.mm.bing.net
Source: tse1.mm.bing.netMany operating systems come with built-in remote access tools that allow you to connect to another computer within the same network or over the internet. For example, Windows operating systems have Remote Desktop Connection, while macOS has the Screen Sharing feature.
These built-in remote access tools often require specific configurations and permissions to be set up on both the client and host machines. However, they provide a convenient option for accessing another computer without the need for additional software installation.
4. Web-Based Remote Access
 Source: tse1.mm.bing.net
Source: tse1.mm.bing.netWeb-based remote access solutions allow you to connect to another computer using just a web browser. This eliminates the need for installing any software on the client machine. These solutions often use HTML5 or Java-based technologies to establish the connection.
Web-based remote access is particularly useful when you need to connect to a remote computer from a device where you cannot install additional software, such as a public computer or a mobile device.
Ensuring Security in Remote Access
 Source: tse1.mm.bing.net
Source: tse1.mm.bing.netWhen accessing another computer remotely over the internet, security should be a top priority. Here are some essential steps to ensure the security of your remote access sessions:
1. Use Strong and Unique Passwords
 Source: tse1.mm.bing.net
Source: tse1.mm.bing.netWhen setting up remote access, it is crucial to use strong and unique passwords for both the client and host machines. Avoid using easily guessable passwords and consider using a password manager to securely store and generate complex passwords.
2. Enable Two-Factor Authentication
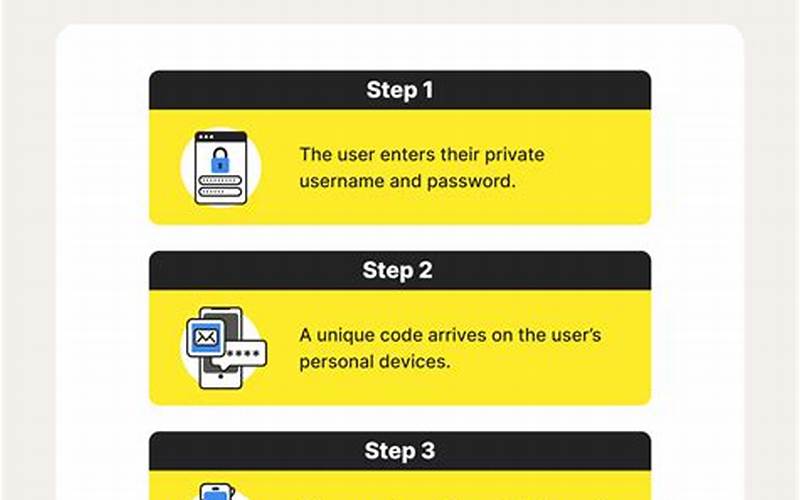 Source: tse1.mm.bing.net
Source: tse1.mm.bing.netEnabling two-factor authentication adds an extra layer of security to your remote access sessions. This requires you to provide a second form of authentication, such as a verification code sent to your mobile device, in addition to your password.
3. Keep Software and Operating Systems Updated
 Source: tse1.mm.bing.net
Source: tse1.mm.bing.netRegularly updating your software, including remote access tools and operating systems, is crucial for maintaining security. Updates often include patches for known vulnerabilities, reducing the risk of unauthorized access.
4. Utilize Encryption
 Source: tse1.mm.bing.net
Source: tse1.mm.bing.netUsing encryption protocols, such as SSL/TLS, ensures that your data transmitted during remote access sessions is encrypted and protected from interception. Always prioritize remote access solutions that offer strong encryption.
5. Be Wary of Phishing Attempts
 Source: tse1.mm.bing.net
Source: tse1.mm.bing.netPhishing attacks can trick users into revealing their login credentials or installing malicious software. Be cautious of any unsolicited emails, messages, or links related to remote access and avoid clicking on suspicious links or providing personal information.
Conclusion
Accessing another computer remotely over the internet provides a convenient way to control and manage a remote machine from anywhere in the world. Whether you choose to use remote desktop software, a VPN, built-in tools, or web-based solutions, always prioritize security measures to protect your data and ensure a safe remote access experience.
Post a Comment for "How to Access Another Computer Remotely over the Internet"